Five Findings from the 2023 IBM Security Cost of a Data Breach Report
I was reviewing the 2023 IBM Security Cost of a Data Breach Report this week and wanted to share some findings I found interesting. This report is...
2 min read
Stephanie Goetz : Updated on July 21, 2023


They’ve come back around…those business email compromises, which were all too common in the late 2010s.
Unfortunately, we have seen many of these in recent weeks, even with multi-factor authentication (MFA) in place. We know that threats evolve, and maybe it’s just me, but I didn’t expect it to happen this fast.
Some of these compromises have been straightforward, a user simply giving up their password and six-digit code to the much more sophisticated Adversary in the Middle (AiTM) attacks. AiTM attacks specialize in getting past MFA protection.
It’s important to note, communicate, and even stress, to our users that these attacks start as an email from a trusted third party who is compromised. From what we’ve seen, these emails come looking like a Microsoft notification requesting a login to SharePoint or another product.
It’s important that the user verify with the source of the request, outside of email, before clicking. Also, be mindful of the URL of the site they are logging into…. better yet, just log in outside of the email link to the trusted site.
Considering a picture is worth 1,000 words, here’s Microsoft’s diagram of how these AiTM attacks work:
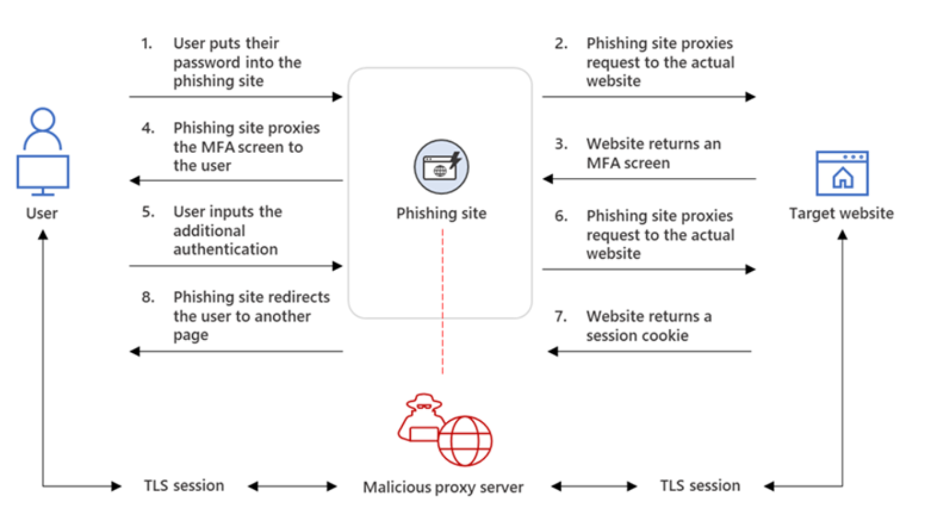
Here are some ways to prevent AiTM attacks against Azure Active Directory and M365. Remember that we still need to protect against other attacks, so remember that these are in addition to what we already do (MFA, training, email filters, etc.).
AiTM attacks have become all too common lately, so please consider spreading the word to your team and considering adding some additional security layers for these attacks. If you need help or have any questions, please contact us at support@bedelsecurity.com.
Great post with more information on the conditional access controls: https://jeffreyappel.nl/tips-for-preventing-against-new-modern-identity-attacks-aitm-mfa-fatigue-prt-oauth/

I was reviewing the 2023 IBM Security Cost of a Data Breach Report this week and wanted to share some findings I found interesting. This report is...

Over the past month, many have written about the latest LastPass breach. If you have not kept up with the breach, you can see the disclosure from...
Reviewing Complementary User Entity Controls (CUECs) is an important part of any financial institution’s third-party management program. However, we...