Control Assessments Vs. Risk Assessments
When we first start working with new institutions, it is not unusual for us to see them struggling because they have focused their efforts on...
3 min read
Chris Bedel : December 20, 2019


In our work, we're finding that banks and credit unions are still struggling to differentiate between vendor risk assessments and information technology or information security risk assessments (IT Risk Assessment).
This blog post will give some simple explanations that will provide clarity to the dynamics between the two.
I think it's easiest to start by defining what each of the assessments are and what their objectives are.
First and foremost, every technology that a bank or credit union deploys needs to have an IT risk assessment performed on it. This is where we determine the risks to the institution by having an asset or an application in place. Regardless of whether it's hosted on premise or is outsourced to a third party service provider.
Ideally, the end result is some rating of residual risk and maybe even an action plan for additional mitigating controls that need to be applied to this asset
The Vendor Risk Assessment looks at the risk involved in outsourcing the given application, process, or relationship. This needs to focus on the idea that your institution loses control of some of the internal processes and that the vendor becomes an extension of your business.
Do they have a similar control environment as you do?
The two are definitely related, but they need to be treated independently of each other.
I often explain outsourcing using a third party as transferring some of the risk to an outside party.
That doesn't mean that the inherent risk goes away. It means that it's now in the hands of someone else. And that's why both of these assessments are important and both have to be done in the proper circumstances.
One example of this might be a bank that is hosting its own internet banking server. It has to make sure its authentication processes are spot on, that monitoring and oversight are good.
It also has to make sure it understands and mitigates the risk of hosting that server.
In most cases, a community bank would be in over their heads and would have a ton of residual risk by hosting that server.
So, outsourcing that to a third party means that the institution is still responsible for knowing what the authentication methods are and what the oversight processes look like.
But now the actual day to day hosting has been offloaded to someone that's really good at doing that. And that's one of the advantages of using a third party service provider.
However, if the institution outsources the hosting of that server to a third party provider that has no experience in the banking space, has no process for patching and updates, doesn't have a formal business continuity plan or Incident Response Plan, or is in poor financial standing we may have a problem.
In the second scenario, the overall risk is likely to increase by outsourcing that application.
It's a balance, and that's why most both must be considered.
Well, the takeaway of this blog post is meant to be that it simplifies the process for your bank or credit union. So, here's a two-step trick that you can walk through yourself anytime you’re considering a new technology (whether in-house or outsourced).
BTW – these should both be done prior to signing a contract or making the purchase.
If you’re more the decision tree type, I’ve attached one below.
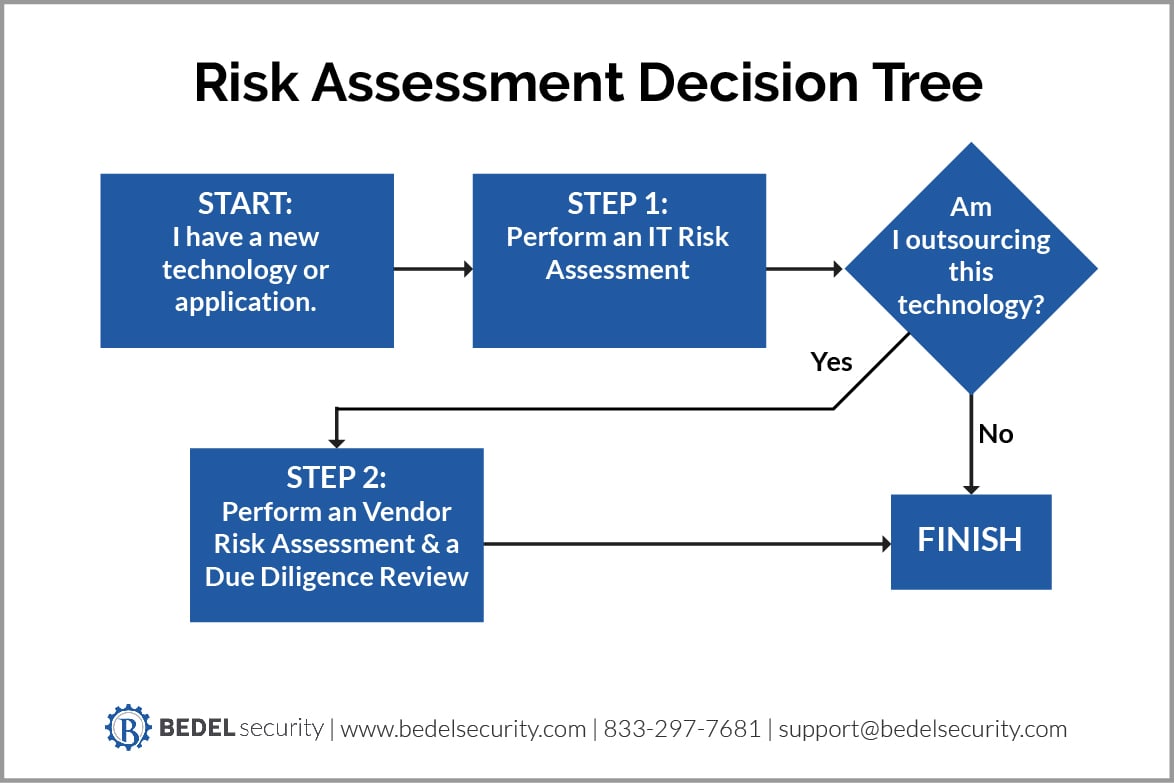
(PLEASE NOTE: as with the example above, you may have planned to keep an application in-house, but during this process you might identify that the residual risk can only be feasibly reduced by outsourcing. We’ve seen this happen, and its part of why we do this first)
Once that's complete move on to step two.
If this asset is being outsourced, perform the vendor risk assessment.
We recommend starting by asking yourself three simple questions:
And based on the answers to those questions you need to perform the appropriate vendor due diligence.
(For more information, see our Simple Vendor Management Quick Reference Guide: https://www.bedelsecurity.com/lp-simple-vendor-management-program-quick-reference-guide)
As I said earlier, there is some overlap between the two. If you are outsourcing the technology, many of the controls that you'll be looking up for the IT risk assessment will come from vendor documentation. You may need to go look at their SOC2 to determine some of the controls that you need to know about. You may need to look at their business continuity plan to ensure that you have your availability concerns covered.
But also keep mind: the 2 processes are independent of one another. A technology that is high risk doesn’t necessarily mean that the associated vendor is high risk. A high risk vendor doesn’t necessarily make the associated asset high risk. I really depends on the circumstances.
It can be a little complicated, but it you follow those two simple steps and take them one at a time, I think it'll make this process easier for you.
If you run into bumps along the way, you can always contact us for help at support@bedelsecurity.com or 833-297-7681.

When we first start working with new institutions, it is not unusual for us to see them struggling because they have focused their efforts on...
When it comes to managing cybersecurity risk in community financial institutions, there’s often confusion between two key activities: the Information...

The cybercriminals are still on top of their game, changing targets and tactics. The work-from-home revolution continues and the drive for automation...