Confessions of a Professional Worrier
A few weeks ago, in my life outside of cybersecurity, a person said to me: “You are always thinking three steps ahead of the rest of us”. I am not...


Today's blog post is about the three major roles of an information security program. And the reason I'm writing this is because we often speak to financial institutions that maybe have one or two of the three roles and think they’re covered.
But the three roles act like legs on a three-legged stool: If you're missing one of the legs, the stool is not going to work very well.
It's the same with your Information Security Program.
We hear things like:
“We outsource our IT, so we’re covered”
Or
“We just signed on with an MSSP, so we don’t need a CISO”
Or
“Our IT Manager handles all of that”
So I think it's really important to understand what each piece does, how they work together, and why they need to operate independently from one another.
The three roles are as follows:
#1 IT & Operations – This function oversees the strategy, implementation, and upkeep of your technology operations. Things like your network, servers, workstations, applications, email, and phone systems. Your core provider and core systems fall under this category.
This can be filled by in-house IT staff, outsourced to a Managed IT provider, or a combination of the two.
We tell our clients all the time that this is the foundation of a secure program. The other 2 roles will not be effective if you don't have this in place.
#2 Monitoring - This is the collection and analysis of logs from your information technology assets, like: internal network monitoring, firewall monitoring, server logs, Active Directory logs, IDS, IPS, email, web filtering, etc.
This function helps to identify breaches, cyber-attacks, or other incidents. It also helps to provide oversight of IT administration. Both are extremely important in today’s threat landscape.
Monitoring needs to be a 24x7x365 service. While it can be done in-house, we’ve found that dedicated outsourcing arrangements for this service are much more effective for community financial institutions.
#3 Chief Information Security Officer (CISO) – This role is responsible for program strategy, oversight, and governance. The CISO helps direct policy and oversees cyber risk management functions. They work with the executive team to ensure that information security aligns with business goals. The CISO is responsible for communicating the status and effectiveness of the overall program to the board of directors.
This role should be filled by a qualified individual and can be a conventional employee or outsourced entity (Virtual CISO, vCISO, Fractional CISO).
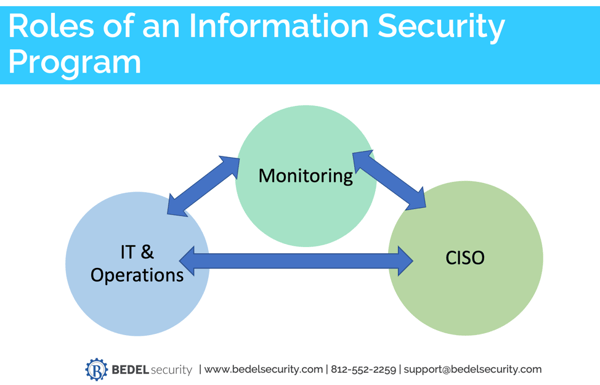
As you can see, each role performs a distinct function and you need every single one for your program to be effective. Ideally, each of these is operating independently from one another.
They need to be independent for 2 reasons:
But while they need to be independent, they also need to work together.
IT works with the CISO to design and implement controls in conjunction with policy. The CISO works with Monitoring to review reports and provide context to management. Monitoring works with IT to investigate and respond to security events and anomalous activity.
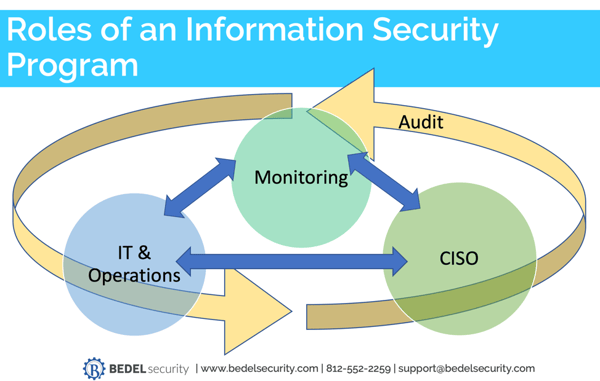
Where does Audit fit in?
Audit plays an important role, but more of a snapshot in time, rather than day-to-day activities. Audit comes in once a year and verifies that the 3 key components are working properly and that other controls are effective as well. It is still ABSOLUTELY NECESSARY, but should not, CAN NOT take the place of any of the other 3.
So, you want to have IT & Operations that is in-tune with the business goals and focuses on delivering technology to achieve those goals.
You want a monitoring component that’s watching your environment all day, every day, and is good at spotting anomalies, and correlating data to discover threats.
You want an experienced chief information security officer that's making sure all the pieces are working together to protect your information assets and meet regulatory requirements.
When those pieces come together and work together, information security becomes less daunting and a lot less painful. And that’s what we’re all looking for.
If you’re not sure if you have each of the roles filled, or how well you have them filled, we can walk you through a quick assessment to help make sure you have the bases covered.
Or if you want help filling the CISO role, we can help you customize a service level that fits your exact needs. Learn more about our CySPOT™ Program here.
Just send us an email at support@bedelsecurity.com to set up a call.

A few weeks ago, in my life outside of cybersecurity, a person said to me: “You are always thinking three steps ahead of the rest of us”. I am not...

This blog post is going to sound a little bit self-serving, but I promise you it's not intended to be that way.