Your Information Security Program Needs Focus
I recently had the chance to speak with Cyrene Wilke, SVP Operations & Technology at Investors Community Bank in Wisconsin on the need for community...
6 min read
Chris Bedel : May 28, 2021


This article is the second of a 2-part series on building an effective outsourcing strategy for the various components of IT for financial institutions. The idea is to share what I’ve seen work over my years of working with multiple institutions. This is not meant to push anyone toward outsourcing - that is a decision that must be made based on the specific circumstances of the organization - and the answer is different for everyone. But, as we are seeing more and more FIs look in this direction, it felt like a good time to explore this topic.
Part 1 talks about why financial institutions need to consider a team of independent entities working together - if you haven’t read that, I suggest you do so first. (You can find Part 1 here.)
The key takeaway from Part 1 is that if you’re going to start outsourcing, you need to find the right balance of partnerships (i.e. vendors) that keep all the parts independent but aren’t so independent that they can’t work together.
The objective of this article is to explain what can be outsourced, help you to identify areas of potential conflict (independence), and give you some ideas on how to manage a group of vendors to work together (Collaboration).
What parts of IT can a financial institution outsource?
While banks and credit unions can’t outsource the decision-making and ownership of risk for their IT operations, we live in an age where just about everything else is on the table.
This is not a fully exhaustive list, as I even removed some for simplicity. It also is not this black and white, as some institutions get very granular in their outsourcing, down to the management of very specific services. Keep in mind, the purpose for defining this list is so we can use it for our independence matrix in the next section, so don’t get too hung up on the details right now.
Core - this covers all core banking services, including deposits, loans, item processing, e-banking, ATM, etc.
IT - this can sometimes be called “Managed IT” or a “Managed Services Provider” (MSP). For our general purposes, we’re defining it as including: helpdesk, network management, server management, patching, procurement and installation, etc.
Audit - this is the testing of general controls for effectiveness, usually performed annually. While it can be coupled with penetration testing, I’ve separated the two for this article.
Penetration Testing - this is the independent testing of the defenses of the network and assets. It should include both external and internal testing. It is more than a vulnerability scan - it is a simulation of a cyber attack, more than just a list of theoretical weaknesses. It is typically done once annually.
Vulnerability Scanning - this is an operational scan of the network for missing patches and other misconfigurations. This should be done at least quarterly, but more frequent is better.
Monitoring - this may also be called a SIEM, or “Managed Security Services Provider” (MSSP). This should be done 24x7x365 by people who know what they are doing. I’ve yet to run across a community bank that should not be outsourcing this. It typically includes network traffic, server logs, endpoint logs, firewall, intrusion prevention, etc.
Datacenter - this is the hosting of servers, routing equipment, and other information assets.
CISO - this is the leadership, strategy, governance, and oversight of the information security and cybersecurity programs. It generally includes policies, risk management, board reporting, incident response, vendor management, etc.
CIO - this role sets the strategy for the organization’s technology and digital objectives. It will work with the other areas listed here to ensure that business goals are being met.
What are the Areas of Potential Conflict?
Looking at the list above, you can begin to see where would make sense to consolidate certain roles. This reduces the number of vendors you have to manage and would help to simplify communications. And, unfortunately, most vendors will gladly provide more services to your institution - either because they just want to be helpful OR they want to grow their business.
BUT - that can get you in trouble. You can’t have someone providing oversight on duties their company performs. You can’t have someone auditing programs that their company helped to design or maintain. You don’t want someone providing “advice” that is really just a sales presentation.
Not a good way to run a business - and regulators will begin to question as to whether these types of management practices lead to a safe & sound environment.
It’s OK - these weren’t as much of a concern years ago. As FIs outsource more and more, it gets harder to tell what makes sense and what can compromise independence.
So I’ve created the matrix below to help sort out what outsourced services can be done by the same company, and which ones would present a conflict. Simply find the service that your using a vendor for on the left-hand side, then find another service in question along the top. If the intersection is green, you’re good to add that service to that existing vendor relationship. If the intersection is red, you need to find someone else to perform one of the services. It is bi-directional, so either way, the answer is the same.
One thing to note: I’m hearing more and more of the idea that service companies are creating “separate divisions” to maintain their independence in some of the areas of red below. While this separation of divisions may “technically” make this “OK”, I would urge you to be very cautious. Organizations looking for “technicalities” typically just want to “check the box” anyway and this article isn’t going to be for them. The matrix below is intended to be used for the financial institutions that want to build solid IT and IS programs, free from the issues that conflicts of interest can create. That being said, it assesses these services at the business level, not at the division, team, or individual level.
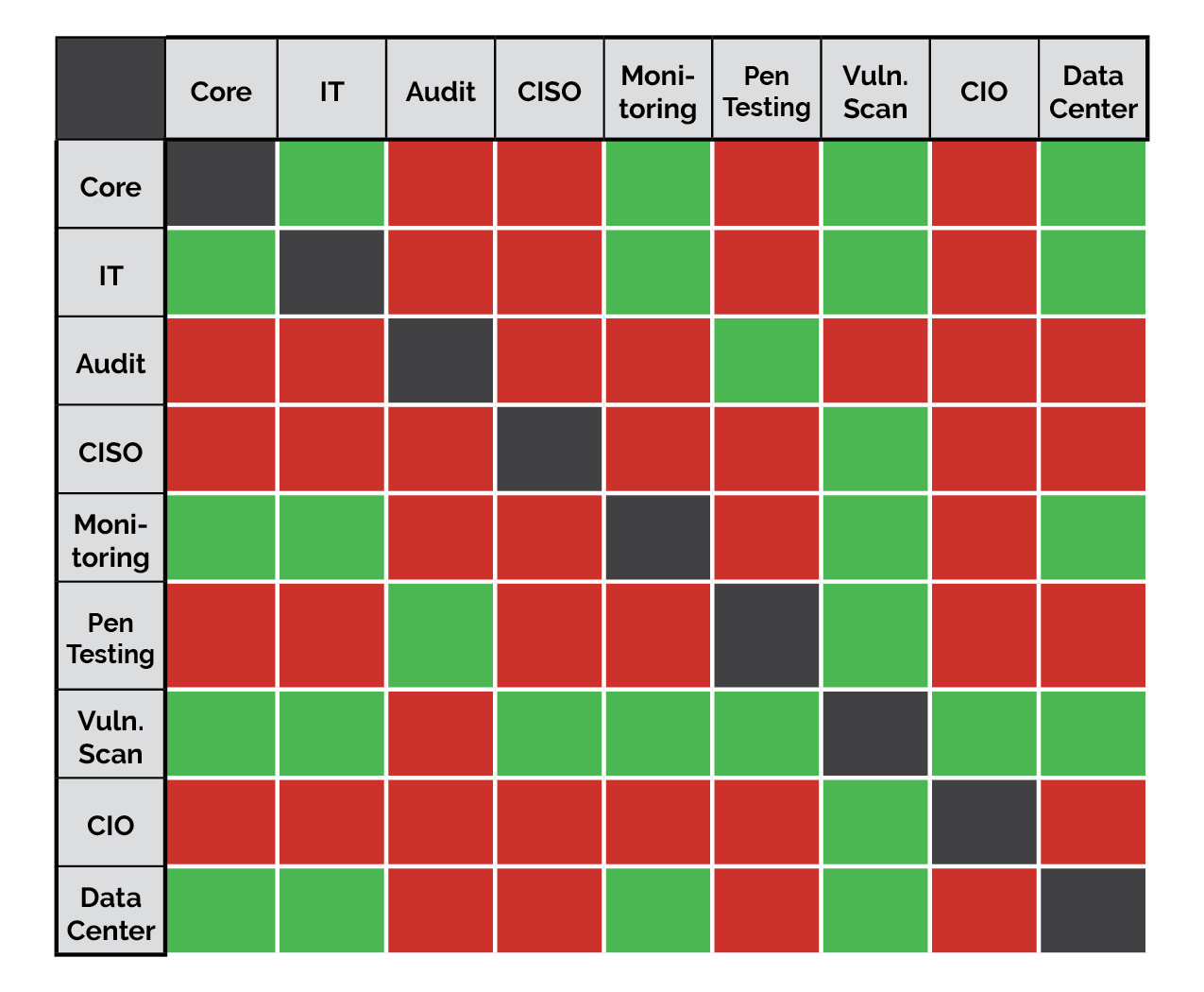
Some examples:
Core In-house, IT and Datacenter outsourced to MSP (including monthly vulnerability scans), Monitoring outsourced to SIEM provider, In-house CIO, Virtual CISO, Annual audit and pen test done by audit firm. Total Outsourced Vendors: 4
Core, Managed IT, Datacenter, and Monitoring outsourced to core provider, In-house CIO, In-house CISO (performs quarterly vuln scans), ITGC audit performed annually by audit firm, annual penetration testing performed by specialty pen testing company. Total Outsourced Vendors: 4
Core Outsourced, IT and Datacenter outsourced to MSP, SIEM Monitoring outsourced to MSSP, Virtual CIO, Virtual CISO, Annual audit and pen test done by audit firm. Total Outsourced Vendors: 6
How do I get this many Vendors working together?
This is where the collaboration comes in. The last thing you want to have is a bunch of vendors that don’t work together - it makes your job harder AND it’s not secure.
When done correctly, you can have the best of both worlds: the specialized skills and expertise to move you in the right direction, but that feels like they are part of a working team.
Here are some tips for building a collaborative culture for your outsourced IT environment:
Conclusion
Outsourcing IT can be a great strategic move for many community financial institutions, but every situation is different. Managing these relationships to achieve “Independent Collaboration” amongst your vendors is worth the effort.
Hopefully, you’ve found this guidance helpful in developing you own strategy or enhancing your existing one.
If you’d like to learn more about this topic, let me know. If you have ideas for a resource that we can create, I’d be happy to consider it. Just contact us at support@bedelsecurity.com.

I recently had the chance to speak with Cyrene Wilke, SVP Operations & Technology at Investors Community Bank in Wisconsin on the need for community...

One of the first things we do when working with a new client is to establish recurring monthly meetings with a set agenda for every meeting. Having...

In case you missed yesterday’s post, here’s a brief recap. If you did read yesterday, you can jump down to cloud based telephony. Keep in mind, this...